Back in the 90s, computer security simply means installing antivirus on every computers in the office. With the rise of the internet, it became Internet Security suites with Firewall, and with the popularity of office servers, it makes more sense to block the threat before it enters and spread through the servers in the company, especially ransomware.
Related Article 😍💰👉 Download Free 60-Days Symantec Endpoint Protection 2025 Trial
What Is an Endpoint? Endpoints are physical devices that connect to a network system such as mobile devices, desktop computers, virtual machines, embedded devices, and servers. For a small to large corporation, this is where Endpoint Management comes into play, not only it prevents, in the case of an emergency it also comes with backup and recovery. It is a central ‘antivirus’ for the entire company. So, which is the best Endpoint Security Platform? Below are 2 comparative report on the performance of various endpoint solutions, just take it with a grain of salt.
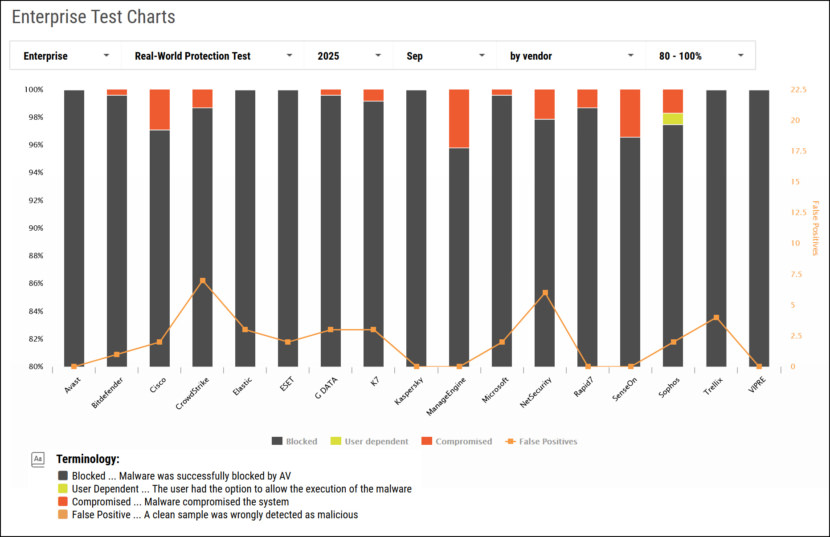
Source: AV-Comparatives’s Enterprise Test Chart for Endpoint
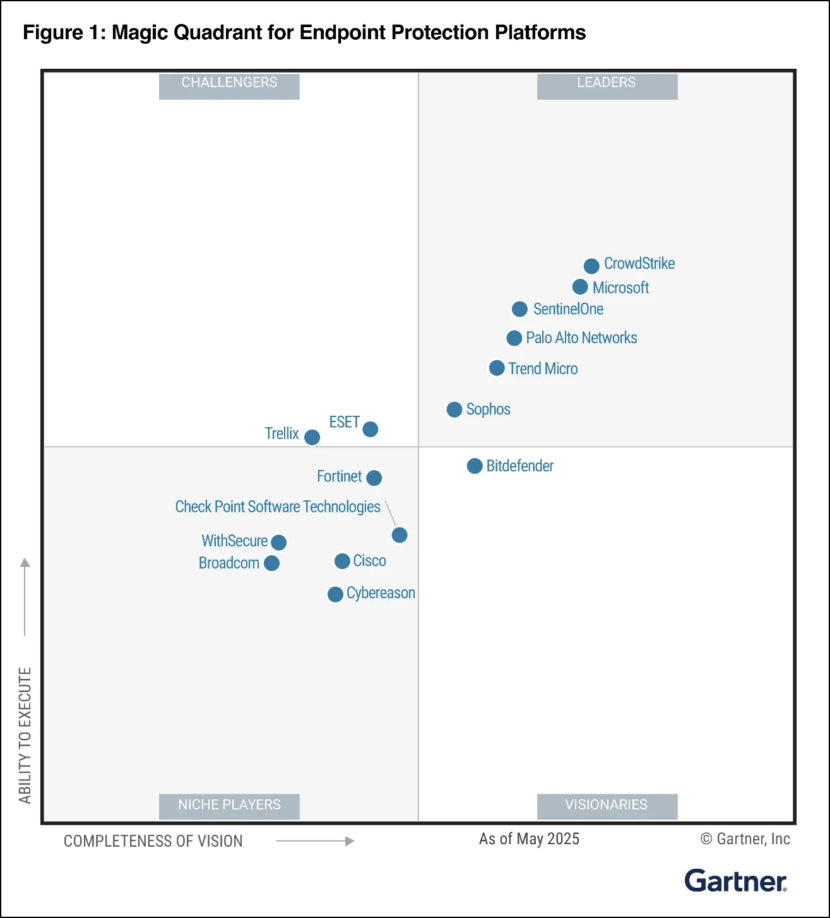
Source: Gartner Magic Quadrant for Endpoint Protection Platforms
The billion dollar question, which ‘brand’ has the best endpoint management solution when it comes to detection, response, prevention, and protection services? It is hard to tell, there is no definite answer, unlike sprinting where you get to see who is the fastest, we can only rely on third party reports.
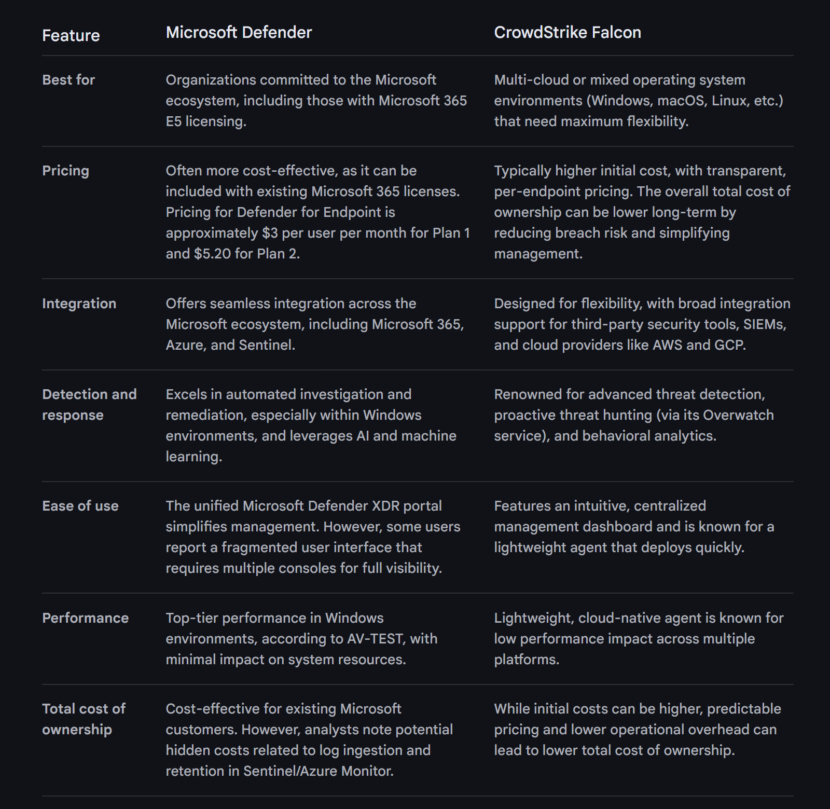
Logically, Microsoft’s Endpoint will always be the best, reason being that with their huge Windows OS installation base and the free Windows Defender on every Windows, they have hundreds of millions of computers sending precious data on the latest threat, all for free to Microsoft, from there with the free data, they are able to better protect their corporate customers with their enterprise endpoint security solutions. From my experience, my choice will be either Crowdstrike or Microsoft, one of the best endpoint protection for business.
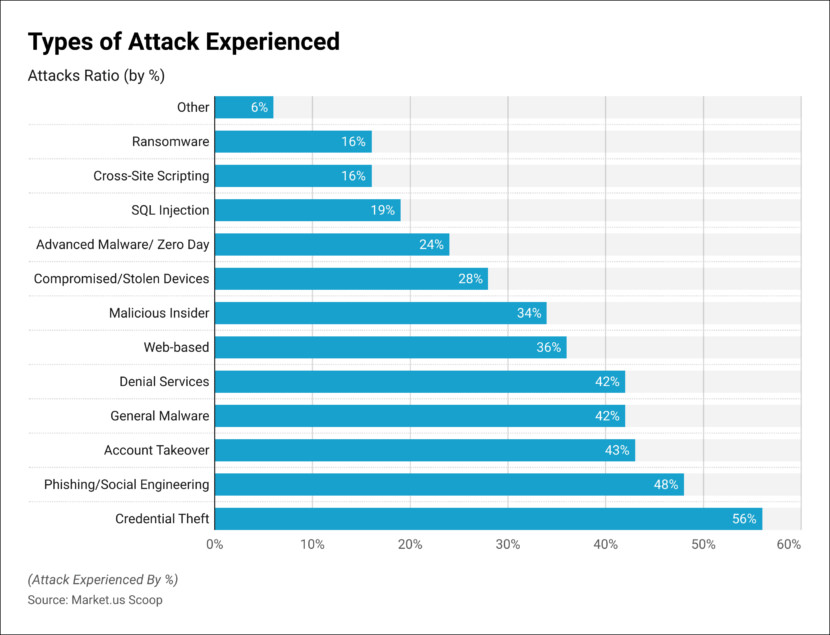
The chart above shows the type of attack stopped by the majority of Endpoint Security Platforms. You should choose the endpoint platform best suit for your company’s requirement.
1. CrowdStrike Falcon
CrowdStrike is a well-established name in the field of cybersecurity, focusing on enterprise risk management through the innovative use of technology. The organization primarily aims to safeguard critical business risk areas, including endpoints, cloud workloads, identity, and data. Utilizing the cutting-edge CrowdStrike Security Cloud and sophisticated AI technology, the company offers effective solutions.
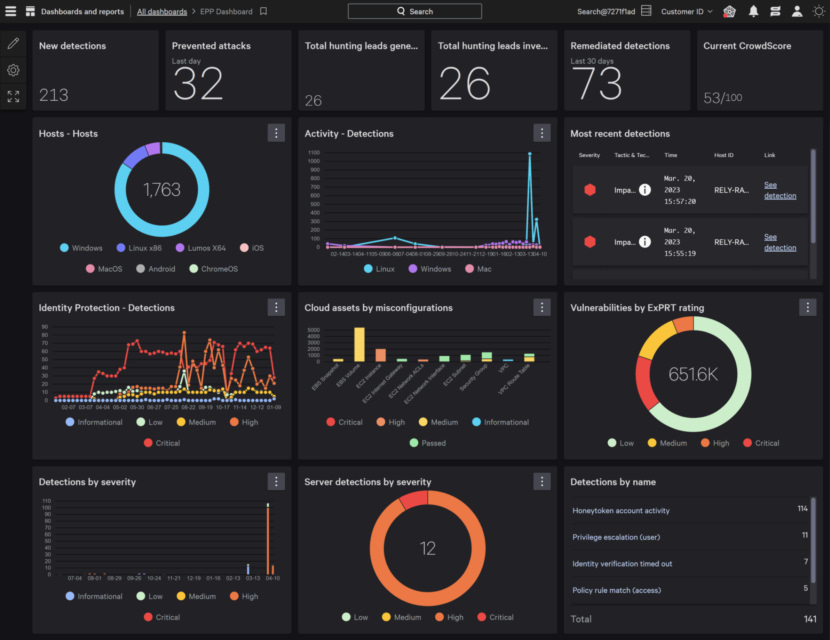
Its CrowdStrike Falcon platform leverages real-time attack indicators, threat intelligence, telemetry enhanced from various enterprise sources, and evolving adversary insights for superior detection, automated protection and remediation, advanced threat tracking, and effective vulnerability visibility.
The Falcon platform, built in the cloud with a unique lightweight-agent architecture, ensures rapid deployment, distinctive protection and performance, and minimized complexity. Consequently, CrowdStrike presents a substantial value proposition from the outset.
2. SentinelOne Singularity Endpoint
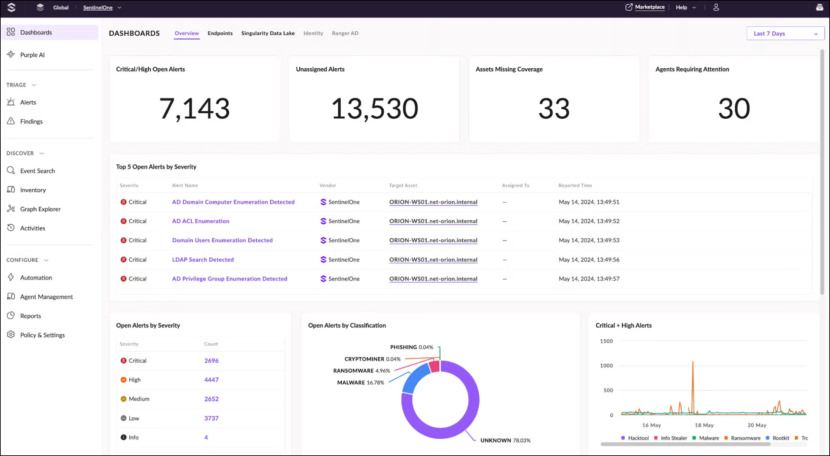
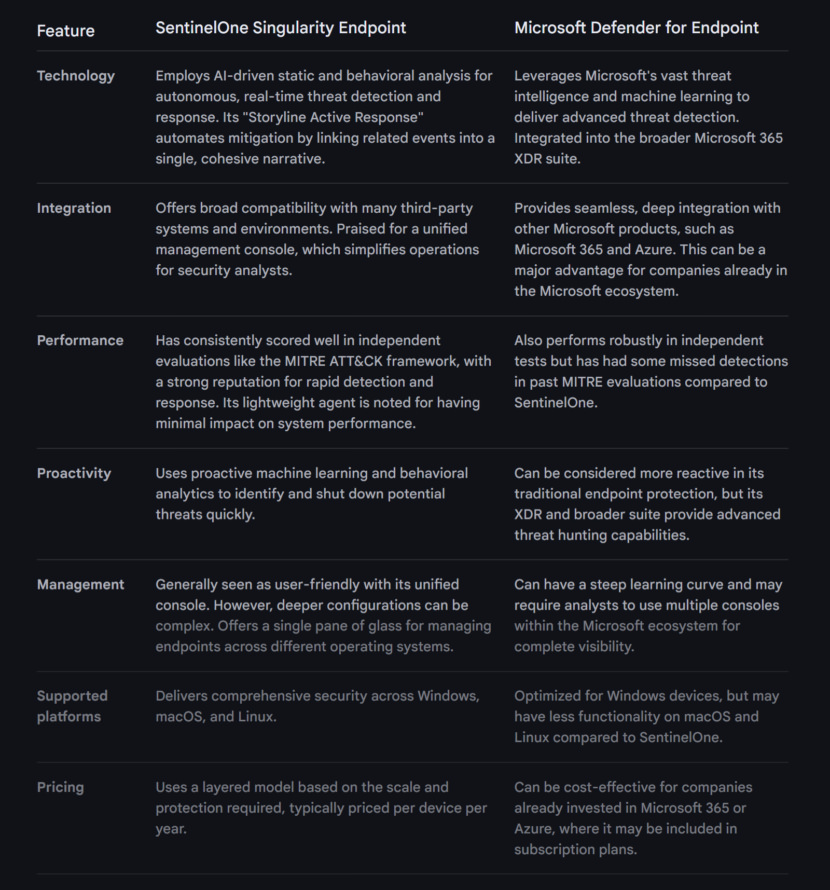
SentinelOne offers autonomous security solutions tailored for diverse IT environments. The primary emphasis of the company lies in endpoint security, cloud security, and identity security. It functions on an AI-driven platform that consolidates data protection, prevention, detection, response, remediation, and forensics into a single framework.
The endpoint security solution employs artificial intelligence to continuously evolve in response to emerging threats, delivering real-time protection and automated responses. A fundamental tenet of SentinelOne’s security strategy is to empower organizations to identify malicious activities across various vectors, swiftly neutralize threats through an integrated response, and perpetually enhance defenses against sophisticated cyber attacks. Additionally, the company delivers a variety of services, including threat hunting, incident response, and incident management.
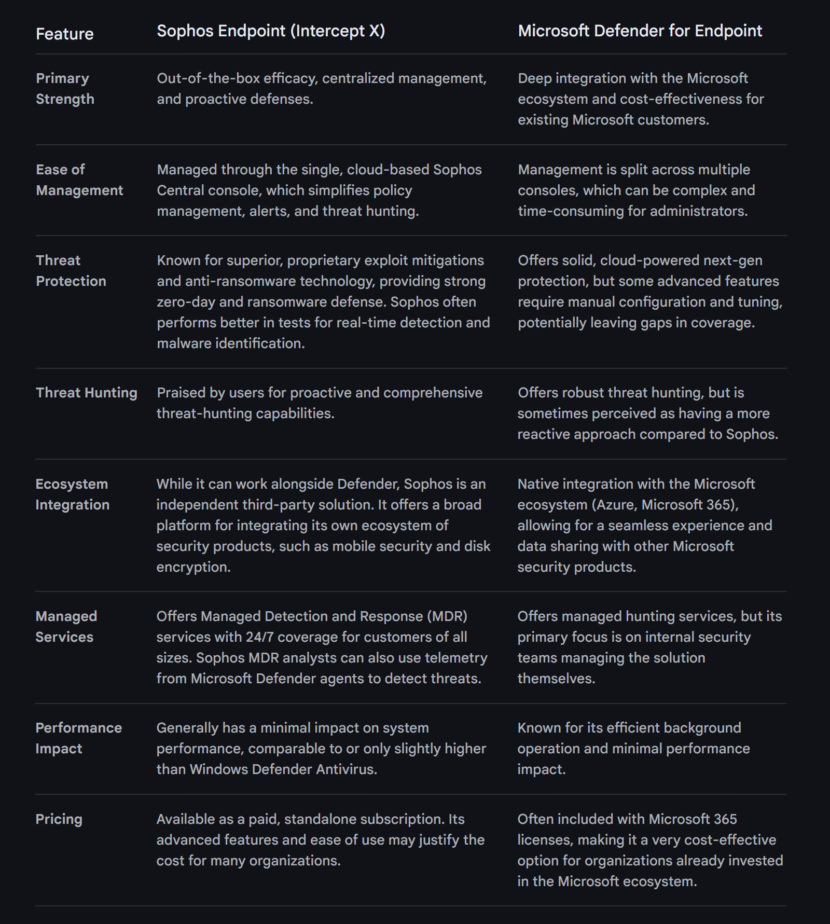
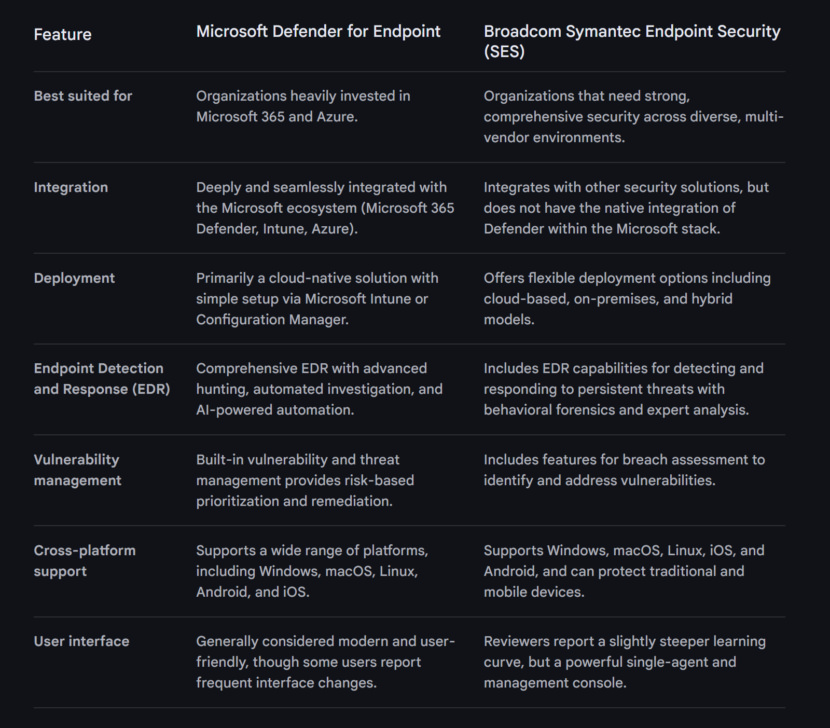
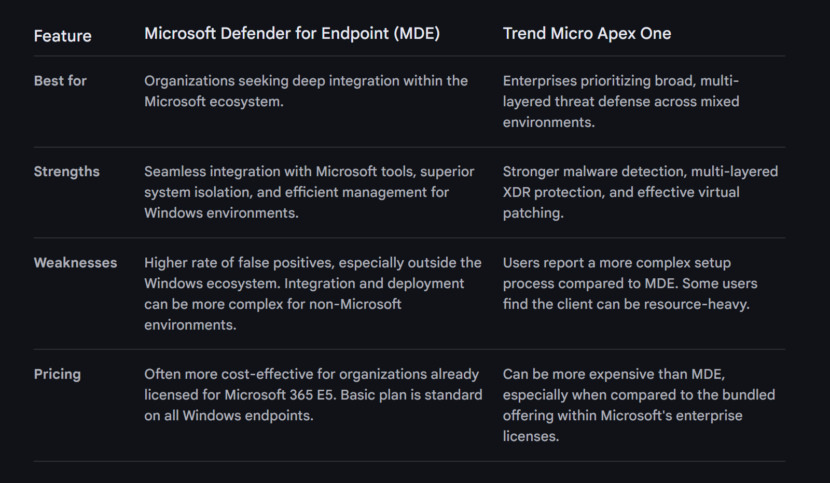
3. Microsoft Defender for Endpoint
Microsoft facilitates digital transformation for the age of an intelligent cloud and an intelligent edge. Its mission is to empower every individual and every organization worldwide to accomplish more. Microsoft is committed to enhancing human and organizational success. Microsoft Security safeguards individuals and data from cyber threats, providing peace of mind.
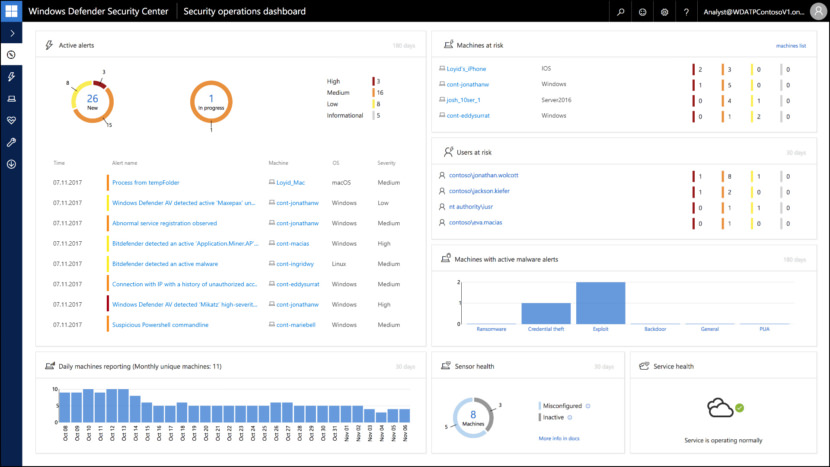
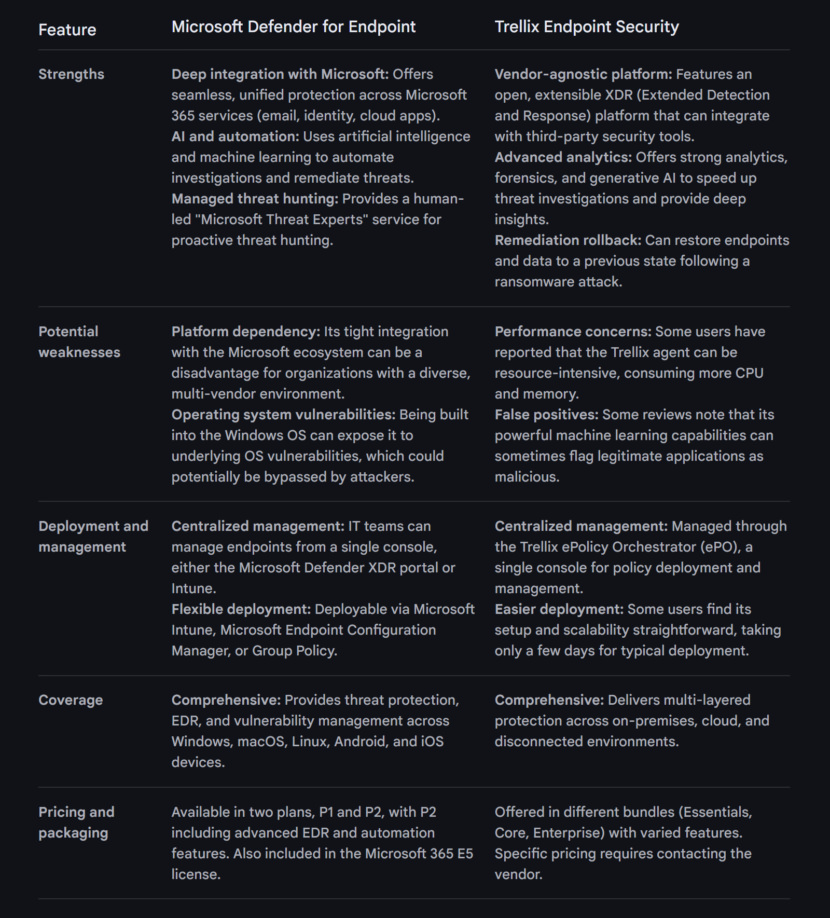
Microsoft Defender for Endpoint is an enterprise endpoint security platform designed to help enterprise networks prevent, detect, investigate, and respond to advanced threats. Example endpoints include laptops, phones, tablets, PCs, access points, routers, and firewalls.
- Endpoint behavioral sensors: Embedded in Windows 10, these sensors collect and process behavioral signals from the operating system and send this sensor data to your private, isolated, cloud instance of Microsoft Defender for Endpoint.
- Cloud security analytics: Using big data, device learning, and unique Microsoft optics across the Windows ecosystem, enterprise cloud products (such as Office 365), and online assets, behavioral signals are translated into insights, detections, and recommended responses to advanced threats.
- Threat intelligence: Generated by Microsoft hunters, security teams, and augmented by threat intelligence provided by partners, threat intelligence enables Defender for Endpoint to identify attacker tools, techniques, and procedures, and generate alerts when they’re observed in collected sensor data.
4. Trellix Endpoint Security Suite
Trellix functions as a global organization committed to transforming the cybersecurity environment. The primary business challenge that the company tackles pertains to the rise of advanced threats confronting organizations in the present day. In response to this, Trellix provides an open and native detection and response platform, establishing a secure and robust operational framework.
The company leverages machine learning and automation, utilizing the skills of its security experts and a broad partner network to implement technological innovations. Their expertise is applied to benefit a wide-ranging user base that includes various business and government entities.
Data Loss Prevention (DLP) and protection – Based on the fundamental principle of preserving data integrity and confidentiality, DLP tools are designed to scan and monitor data while it is in transit, at rest, and during processing. They utilize sophisticated detection methods to pinpoint potential leaks or unauthorized data transfers in accordance with established policies. When a possible policy violation is identified, the DLP system can respond by notifying administrators or completely blocking the data transfer. This system not only prevents accidental leaks caused by human mistakes but also hinders malicious efforts by insiders or malware to extract data.
5. Sophos Intercept X Endpoint
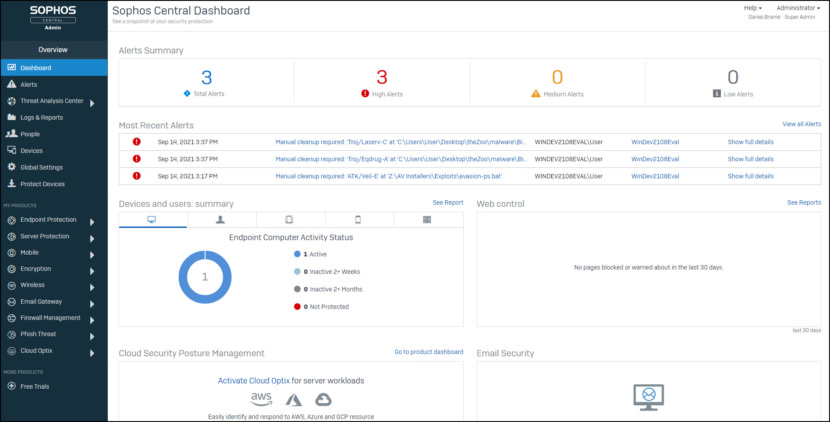
Sophos is an AI-powered endpoint security, a worldwide provider of sophisticated cybersecurity solutions. Their primary emphasis is on delivering a comprehensive array of security technologies, which includes Managed Detection and Response (MDR), incident response services, as well as systems for endpoint, network, email, and cloud security.
These products and services are crafted to assist organizations in combating a variety of cyber threats, including active adversaries, ransomware, phishing, and malware. The company provides fully-managed, turnkey security solutions, offering cybersecurity-as-a-service to organizations across the globe.
In addition, Sophos operates a cloud-based management console, referred to as Sophos Central, and supports the Sophos X-Ops, a cross-domain threat intelligence unit. This unit enhances the Sophos Adaptive Cybersecurity Ecosystem by optimizing its centralized data lake with a robust set of open APIs. Sophos’ operations are distributed globally, with the company’s headquarters located in Oxford, U.K.
6. Symantec Endpoint Security Complete
Broadcom Inc. is a global entity focusing on the design, development, and supply of semiconductor and infrastructure software solutions. Through these operations, the firm addresses the primary issue of providing efficient top-notch technology-based solutions.
Symantec Endpoint Security (SES) Complete delivers comprehensive protection for all your traditional and mobile devices across the entire attack chain. Symantec endpoint innovations include behavioral isolation, Active Directory security, and Threat Hunter technologies to protect your endpoints against sophisticated threats and targeted attacks. For higher return-on-investment and lower total cost of ownership, this single-agent solution supports on-premises, hybrid, and cloud-based deployments.
Tools such as Endpoint Detection and Response (EDR) assist in monitoring and addressing potential threats in real-time, offering essential defense mechanisms against sophisticated attacks. Moreover, Virtual Private Networks (VPNs) are vital in encrypting internet traffic, especially for individuals connecting through unsecured networks like public Wi-Fi hotspots.
Furthermore, Multi-factor Authentication (MFA) strengthens these platforms by introducing an additional layer of verification, guaranteeing that only authorized users can access sensitive systems.
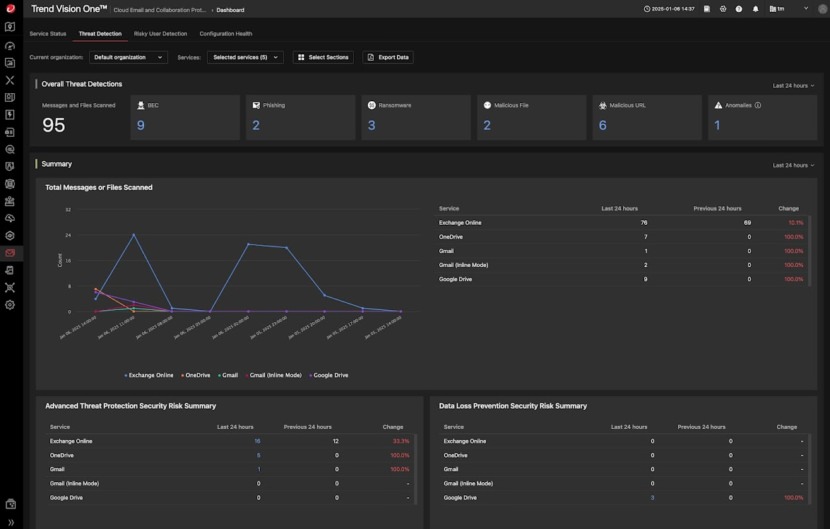
7. Trend Vision One Endpoint Security
Trend Micro is an international organization that focuses on cybersecurity. With extensive experience and global threat analysis, the main business challenge the company tackles is digital security. Its cybersecurity platform is crafted to safeguard a multitude of organizations and individuals across various clouds, networks, devices, telecommunication and endpoints.
The core area of operation lies in cloud and enterprise cybersecurity, recognized for delivering advanced threat defense strategies suitable for different platforms. Furthermore, the company provides centralized visibility for rapid and enhanced detection and response. The threat research team within the company offers critical intelligence and insights, thereby enhancing the efficacy of the cybersecurity platform and aiding global organizations in their fight against cyber threats.
With a workforce of 7,000 employees distributed across 65 countries, the company’s primary objective is to help organizations secure their interconnected world.
8. ESET Endpoint Protection
ESET is a globally recognized, science-oriented digital security firm located in the European Union, with over 30 years of experience in malware research and technological innovation. ESET employs a validated, multi-layered strategy for cybersecurity that integrates long-established machine learning techniques, a cloud-enhanced reputation system, and human expertise to facilitate the prevention, detection, and response capabilities of the ESET PROTECT Platform.
ESET’s offerings range from contemporary endpoint and mobile security to extended detection and response, encryption and authentication, as well as cloud-based threat defense. They effectively prevent unknown threats and provide comprehensive security services, ensuring unobtrusive protection and monitoring around the clock. This enables real-time updates to defenses, safeguarding both businesses and users, all managed through either cloud-based or on-premises security management.
- Network Attack Protection – ESET Network Attack Protection improves detection of known vulnerabilities on the network level.
- Brute Force Attack Protection – Detects and blocks automated attacks that try to use password guessing techniques to gain access to your network.
- Stop fileless attacks – ESET endpoint protection platforms have mitigations in place to detect malformed or hijacked applications to protect against fileless attacks.
- Safeguard the web browser – Designed to protect an organization’s assets with a special layer of protection that focuses on the browser, as the main tool used to access critical data inside the intranet perimeter and in the cloud.
9. ThreatDown Endpoint Detection and Response
Malwarebytes is a worldwide cybersecurity firm that provides endpoint protection, privacy, and threat prevention solutions across the globe. With decades of expertise as the final line of defense against the latest malware, Malwarebytes has gained the trust of millions of individuals and organizations to thwart threats at every phase of the attack lifecycle, secure digital identities, and protect data and privacy.
ThreatDown, which is powered by Malwarebytes, streamlines intricate security processes by merging detection and remediation with rapid deployment and a user-friendly interface – all within a single scalable solution, utilizing one agent and one console – to safeguard individuals, devices, and data in just minutes. The company is based in California and has offices in Europe and Asia.
Restore encrypted, deleted, or modified files up to 7 days after an attack. The Patented Linking Engine removes all malware traces, artifacts, and configuration changes returning devices to a healthy state and preventing ransomware reinfection.
10. Harmony Endpoint
Check Point Software Technologies Ltd. is an organization that provides cybersecurity solutions to governmental and commercial entities globally. The solutions offered by the company are intended to protect against a range of cyber threats, such as malware and ransomware.
Utilizing Check Point’s multilevel security framework, known as ‘Infinity Total Protection with Gen V advanced threat prevention’, the cloud, Healthcare, Hospital, and Biotech network, and mobile devices of businesses are secured. Furthermore, Check Point offers a thorough and user-friendly security management system for control.
11. Aurora Endpoint Security
Arctic Wolf envisions a future without cyber risk. Every organization should be so effective at security operations that both the likelihood and impact of a cyber attack is minimized to the point where risk is essentially zero. Arctic Wolf’s Mission: End Cyber Risk.
Aurora Endpoint Security delivers powerful, AI-driven defense against modern threats. Designed to be easy to use and highly effective, whether on its own or with 24×7 monitoring, Aurora Endpoint Security offers flexible deployment options so you can strengthen your defenses and ultimately, protect your organization from costly breaches.
By utilizing machine learning algorithms, Endpoint Detection and Response (EDR) systems are capable of continuously acquiring knowledge from extensive datasets, identifying patterns and behaviors linked to malicious activities. This ongoing learning process facilitates the recognition of previously unrecognized threats, thereby improving the system’s ability to detect zero-day vulnerabilities and advanced persistent threats. In addition to detection, artificial intelligence also improves the response component of EDR.
- Zero-day threat prevention with immediate attack containment
- Lightweight endpoint agent for minimal system impact
- Full protection with or without Internet connectivity
- Behavioral Detection Engine that lowers operational overhead and enables the ability to implement automatic response actions
12. Bitdefender GravityZone
Bitdefender focuses on the field of cybersecurity, offering solutions to prevent, detect, and respond to global threats. Serving customers including consumers, businesses, and public sector organizations, Bitdefender acts to eradicate threats, safeguard privacy and information, and strengthen cyber resilience.
Major commitments are made to research and development, with Bitdefender Labs identifying hundreds of new threats per minute and assessing billions of threat queries on a daily basis. Bitdefender has introduced transformative innovations in various areas, including anti-malware, IoT security, behavioral analytics, and artificial intelligence. Established in 2001, Bitdefender operates in 170 countries through multiple offices worldwide.
13. Palo Alto Networks Cortex XDR
Palo Alto Networks is a global cybersecurity organization shaping the future of cloud-centric technology. The main business objective is to provide effective cybersecurity solutions, maintaining and valuing the digital way of life. It addresses the significant issue of maintaining digital security in an increasingly online-centric world.
The company utilizes innovative approaches leveraging advancements in artificial intelligence, analytics, automation, and orchestration. Offering an integrated platform and bolstering a burgeoning ecosystem of collaborators, it assures protection across various platforms including clouds, networks, and mobile devices. The organization envisions a progressively safe and secure digital world each day.
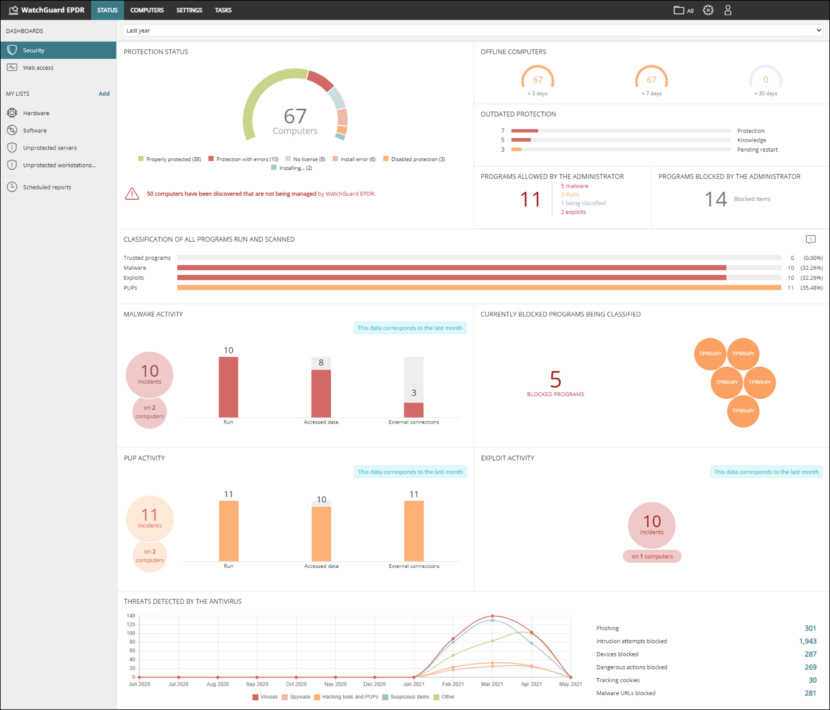
14. WatchGuard EPDR
Palo Alto Networks is an international cybersecurity firm that is influencing the future of cloud-based technology. The primary goal of the business is to deliver efficient cybersecurity solutions while upholding and appreciating the digital lifestyle. It tackles the critical challenge of ensuring digital security in a world that is increasingly focused on online activities.
The company employs innovative strategies that harness the power of artificial intelligence, analytics, automation, and orchestration. By providing a comprehensive platform and supporting a growing network of partners, it guarantees protection across multiple platforms, including cloud services, networks, and mobile devices. The organization aspires to create a progressively safer and more secure digital environment each day.
Self-learning AI detects IoAs, scripts, malware, ransomware, and fileless attacks, while ML analysis of installers, PDFs, and Office files blocks hidden threats. With this service, processes are classified as either malware or as trusted prior to letting only the trusted execute on each endpoint, thereby enabling the ultimate default-deny posture.
15. Carbon Black Cloud
Broadcom Inc. is a global entity focusing on the design, development, and supply of semiconductor and infrastructure software solutions. Through these operations, the firm addresses the primary issue of providing efficient top-notch technology-based solutions. Next-gen antivirus and behavioral EDR. Analyze attacker behavior patterns over time to detect and stop never-before-seen attacks, whether they are malware, fileless or living-off-the-land attacks.
The Carbon Black Cloud is a cloud-native endpoint protection platform (EPP) that provides what you need to secure your endpoints using a single, lightweight agent and an easy-to-use. Enterprise EDR provides immediate access to the most complete picture of an attack, reducing lengthy investigations from days to minutes.
- Combine custom and third-party sources of threat intelligence with our world-class cloud analytics for the clearest possible view of the threat landscape.
- Upgrade to a modern, cloud native solution that offers crucial protection from today’s most widespread and advanced ransomware attacks.
- Enable your team to spend less time tuning policies across disparate tools and more time proactively securing your environment.
- Implement a data-driven approach to alert prioritization and a unified view of security events across the organization.
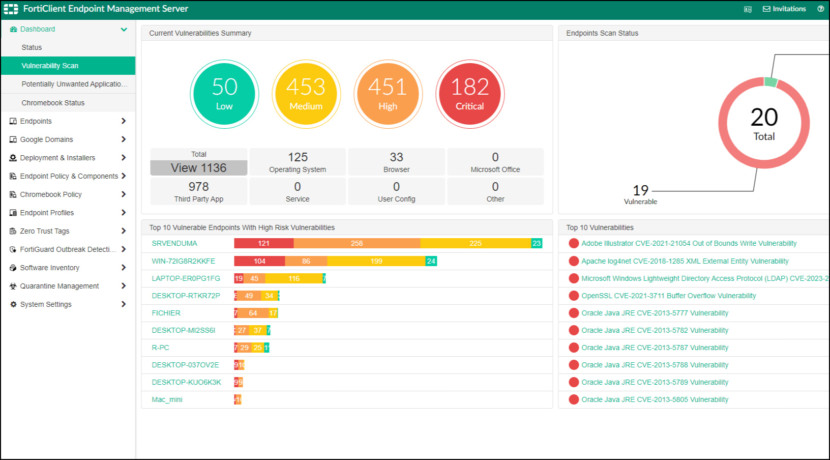
16. FortiClient Unified Endpoint Agent
Founded more than 20 years ago in Sunnyvale, California, Fortinet continues to be a driving force in the evolution of cybersecurity and the convergence of networking and security. Securing people, devices, and data everywhere is our mission. To that end, our portfolio of over 50 enterprise-grade products is the largest integrated offering available, delivering proven cybersecurity everywhere you need it. More than 680,000 customers trust Fortinet solutions, which are among the most deployed, most patented, and most validated in the industry.
Whether it concerns predictability, reused credentials, or brute-force attempts, passwords frequently emerge as the most vulnerable element. Even dedicated protocols such as Remote Desktop Protocol (RDP) are not immune, as attackers actively search for exposed RDP ports to take advantage of. Additionally, email attachments, particularly those containing macros, along with content disseminated on social media and messaging applications, pose considerable threats.
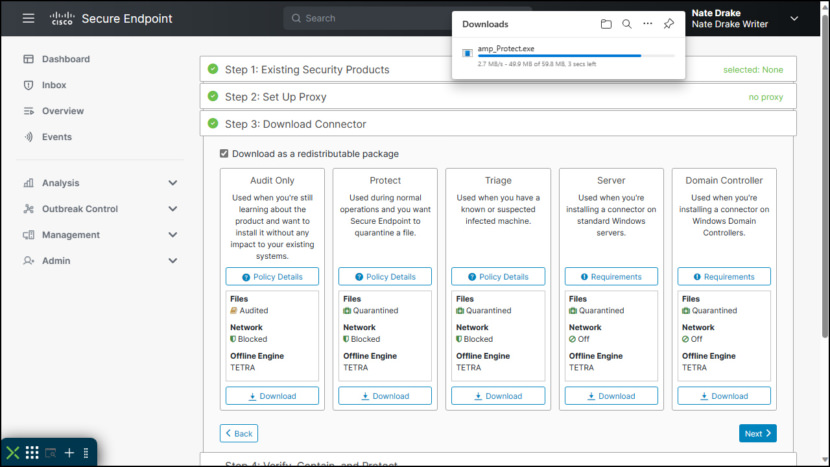
17. Cisco Secure Endpoint
Cisco is a corporation that focuses on networking technologies, especially solutions based on Internet Protocol (IP). Founded in 1984 by a collective of computer scientists from Stanford University, Cisco has developed a global workforce and continues to drive innovation across various sectors, particularly in routing and switching.
In addition to its primary business, the company explores emerging technologies such as home networking, IP telephony, optical networking, security features, storage area networking, and wireless technology. Furthermore, Cisco leverages its expertise to provide a comprehensive array of services, including technical support and advanced services. The company markets its products and services at an enterprise level, catering to Banking and Finance commercial businesses, service providers, and end-users.
18. Cybereason Defense Platform
Cybereason is an organization established to enhance cyber defense, providing extensive protection against attacks. The company addresses a significant challenge in the industry – unified security – spanning from individual endpoints to complete enterprises.
The Cybereason Defense Platform integrates detection and response mechanisms, advanced anti-virus solutions, and threat hunting initiatives, to offer a thorough analysis of all components involved in a malicious operation.
The goal is to enable the eradication of cyber attacks, ranging from isolated endpoints to expansive networks. Cybereason, a privately held entity, maintains a global network that originates from its headquarters in Boston.
19. Webroot Business Endpoint Protection
Webroot, a subsidiary of OpenText, leads the way in the best endpoint protection for business employing cloud technology and artificial intelligence to promptly prevent zero-day threats. The company provides endpoint protection, network security, and training solutions focused on security awareness, specifically designed for small enterprises and managed service providers.
By leveraging the capabilities of machine learning, Webroot is committed to protecting a wide array of businesses and individuals in an interconnected world. In 2019, OpenText, a worldwide leader in Enterprise Information Management, acquired Webroot along with its partner organization Carbonite. Together, they deliver extensive endpoint protection and disaster recovery services, establishing a robust presence in the realm of cyber resilience.
- Protects against file-based and fileless script attacks
- Blocks malicious JavaScript, VBScript, PowerShell, macros, and more
- Enables admins to detect scripts running in their environments
- Allows whitelisting for legitimate scripts
20. Cynet Endpoint Security
Cynet endpoint security for business is a comprehensive cybersecurity platform powered by AI, specifically tailored for lean teams and offered through a global network of partners. Its integrated platform brings together vital security features—including endpoint protection, email security, network detection, user identity management, deception technology, mobile, SaaS, and cloud security, as well as automated response—into one cohesive and user-friendly solution.
Driven by CyAI and supported around the clock by CyOps security professionals, Cynet significantly shortens the time required for detection and response, reduces overall ownership costs, and simplifies operations. By minimizing the number of tools to oversee, decreasing the volume of alerts to investigate, and automatically neutralizing more threats, Cynet grants organizations the cybersecurity assurance they need to concentrate on their core objectives.
21. Kaspersky Next EDR Foundations
Unbeatable endpoint protection that keeps your business safe from ransomware, fileless malware and emerging threats. As your business expands, fortify your cybersecurity at every stage with Kaspersky Next, our product line built to defend against the onslaught of sophisticated and emerging cyberthreats.
Build cost-efficient security services based on products our customers love. Minimal investment required, just choose our cloud-based solutions to serve your small and medium business customers. Kaspersky’s endpoint management system award-winning MSP program and MSP-ready security are tailormade to address your customers’ most common security pains.
- Anti-Ransomware
- Network Security
- Cloud Monitoring
- Cloud Security
- Task Optimization
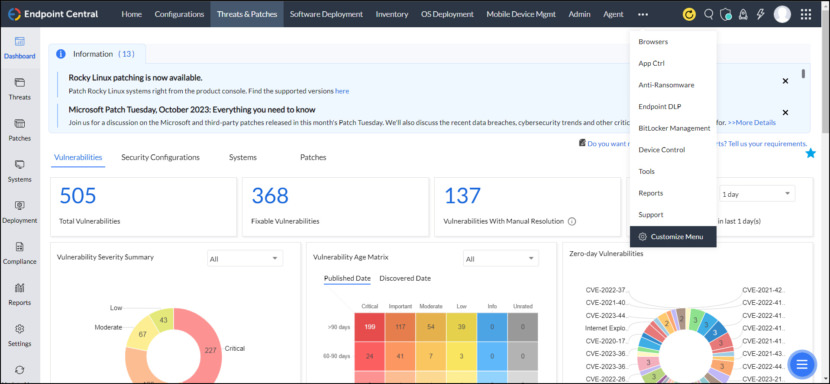
21. ManagedEngine Endpoint Central
As the enterprise IT management division of Zoho Corp., ManageEngine empowers you to take control of your IT, from your security, networks, and servers to your applications, service desk, Active Directory, desktops, and mobile devices.
ManageEngine offers you more than 60 enterprise endpoint privilege management solutions products and over 60 free tools for identity and access management, enterprise service management, unified endpoint management and security, IT operations management, security information and event management, advanced IT analytics, and low-code app development. Your deployment options include on-premises, cloud-native, cloud-ready, and MSP models.
Do not underestimate their duty to protect you from cybercrime or from regulatory transgressions. Their certifications include ISO/IEC 27001, ISO/IEC 27701, ISO/IEC 27017, ISO/IEC 27018, ISO/IEC 20000, and AICPA/SOC.

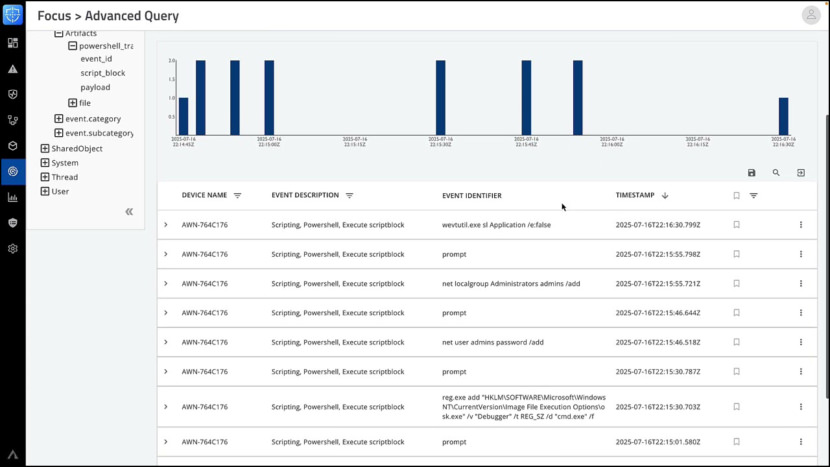
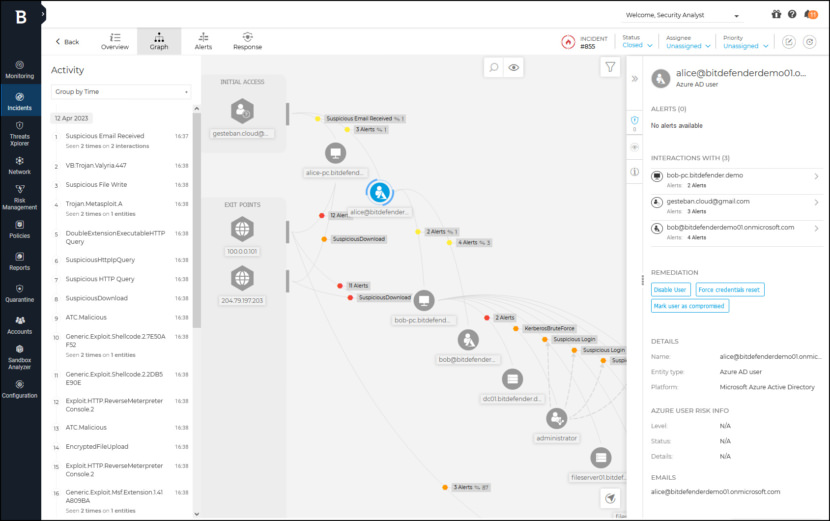
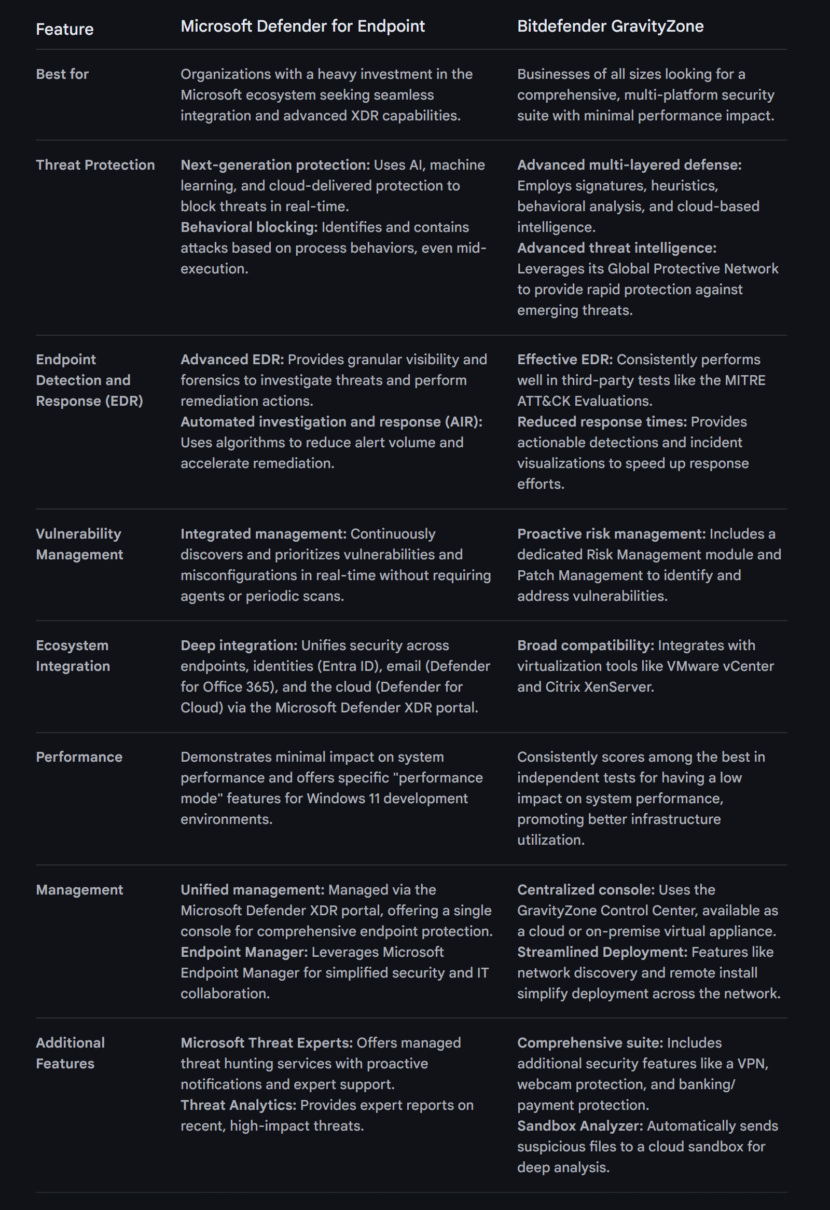
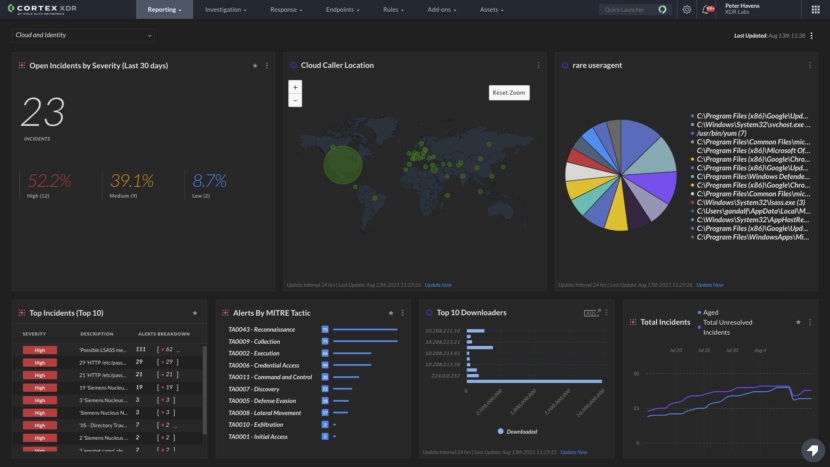



![Download ESET Endpoint Antivirus For Business [ Best Security Protection ]](https://www.geckoandfly.com/wp-content/uploads/2018/03/530-eset-logo-120x120.jpg)
