Is my email address and password hacked? The only way to find out is to use these ‘Reverse Search Engine’ to query your own email addresses or favorite password, you’ll be surprised to find your ‘Unique’ password is searchable. I’ve tested all of these sites personally and my so-called unique password is not unique. Always change your password every 6 to 12 months, this is because new data is being stolen every day and sold.
Continue ➤ 10 Best Free Password Manager Software & Desktop Cloud App Management
How to protect yourself? Today’s email services and various accounts allow you to use the 2FA feature, 2FA is Two Factor Authentication or multi-factor authentication (MFA) is an additional security layer whereby you are required to input an additional 6 digit security code SMS to your phone. Enable this feature whenever it is available, Gmail, Hotmail, Yahoo Mail, Facebook, Twitter, Instagram, Amazon and more all have this feature.
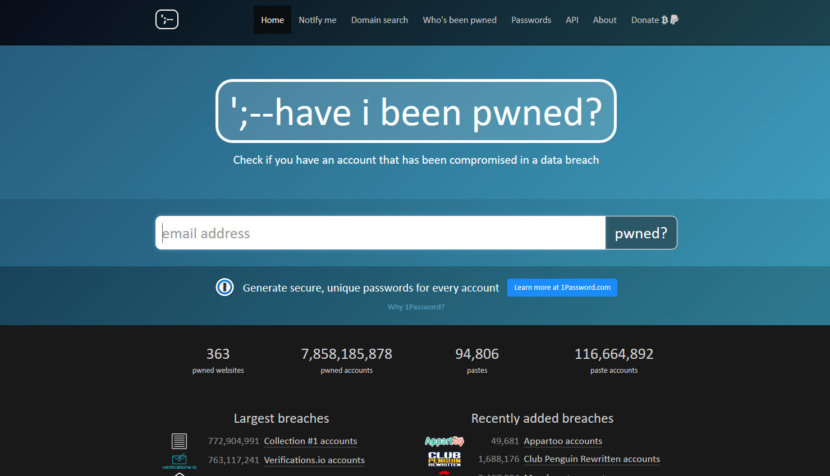
1. Have I been pwned?
Have I been pwned? is a site to check if you have an account that has been compromised in a data breach. The site came about after what was, at the time, the largest ever single breach of customer accounts — Adobe. In short, it is a reverse search engine that will check your email or password against a huge list of stolen data from various sources. To know if any of your accounts was compromised, just search for your own email address or password.
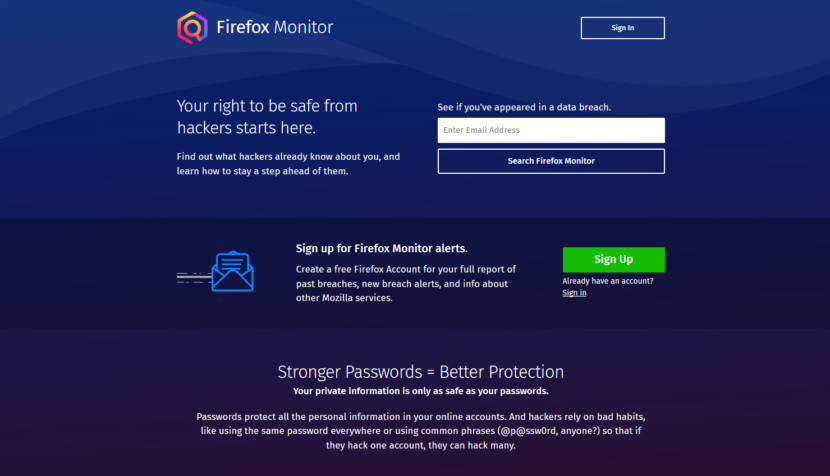
2. Firefox Monitor by Mozilla
Have your accounts been leaked or stolen in a data breach? Find out at Firefox Monitor. Search their database and sign up for alerts. You’ll get a full report on your compromised accounts and notifications any time your accounts appear in new data breaches. A data breach happens when personal or private information gets exposed, stolen or copied without permission. These security incidents can be a result of cyber attacks to websites, apps or any database where people’s personal information resides. A data breach can also happen by accident like if someone’s login credentials accidentally get posted publicly.
3. DeHashed
DeHashed is a hacked-database search-engine created for security analysts, journalists, security companies, and everyday people to help secure accounts and provide insight on database breaches and account leaks. Protect yourself before it’s too late, don’t wait until you’re hacked.
What can you search for? Their advanced systems and huge database allows you to search for IP addresses, emails, usernames, names, phone numbers, VIN numbers, addresses; and what makes them even more unique is they allow you to reverse search passwords, hashes, and more!
4. Inoitsu Email Address Breach Analysis
Use this free service to see if an email address is in any hacked data from known breaches. Get a summary of what specific information may be at risk, critical personal identity alerts, a relative exposure rating and more. Results are shown immediately – no verification, upgrades or extra steps required. Email addresses are not saved after analysis.
5. Password Checkup by Google
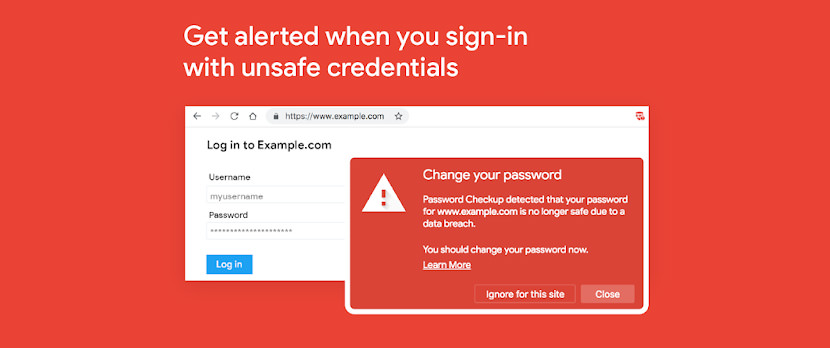
Password Checkup helps you rescue accounts that were affected by data breaches.
Wherever you sign-in, if you enter a username and password that is no longer safe due to appearing in a data breach known to Google, you’ll receive an alert. Please reset your password. If you use the same username and password for any other accounts, please reset your password there as well.
At a high level, Password Checkup needs to query Google about the breach status of a username and password without revealing the information queried. At the same time, they need to ensure that no information about other unsafe usernames or passwords leaks in the process, and that brute force guessing is not an option. Password Checkup addresses all of these requirements by using multiple rounds of hashing, k-anonymity, and private set intersection with blinding.
6. NordPass by NordVPN
Measure the strength of your password with their password strength checker. You’ll also find out whether your unique password was exposed to any known data breaches. A password checker is a web tool that helps you evaluate your password strength. It analyses the syntax of your password and informs you about its weaknesses. Also, it checks the database of breached passwords and flags if your passwords have been compromised in any brute-force or dictionary attacks.
7. Personal Data Leak Checker
Find out if your email and related personal information could get into the wrong hands. Find out how to keep your data secure. Their checker has a 500 GB database of hashed emails that have been leaked.
8. GhostProject
[ Discontinued ] GhostProject.fr is a Fastest Free Database Lookup of Recent 1.4 billion password breach compilation, GhostProject allows you to Search by email or username. The database was recently updated with the last set of data and the total amount of credentials (usernames/clear text password pairs) is 1,400,553,869. To protect yourself, you are strongly advised to stop reusing passwords across multiple sites and always keep strong and complex passwords for your various online accounts. If possible use programs like KeePass or two-factor authentication to generate strong passwords and change them at least once a year.
How To Protect Your Account From Being Hacked!
How To Hack Hotmail Gmail? You can’t! If you need to Google on how to hack Gmail or Hotmail, chances are, it is beyond your knowledge. There is no magical one click button software that does this sort of hacking, furthermore, Google and Microsoft takes security very seriously, therefore if any bugs exist, they are patched immediately.
A) Investigate / Recent Activities
Ever wonder if your ex-boyfriend or ex-girlfriend has access to your email or Facebook and is secretly logging into your account without you knowledge? For those seeking knowledge on how to perform illegal access to someone’s account, be warned that this is illegal and will land you in jail.
Both Google and Hotmail have an activity page that lists the date and time, location, devices and type of activity. Keep in mind that if you use a mobile device, your location may not be reliable. This is because mobile phone services route your activity through different locations. This can make it look like you signed in from somewhere you’re not.
- Google Recently Used Devices – Devices that have been active on your account in the last 28 days, or are currently signed in.
- Microsoft Recent Activity – The recent activity page shows info about when and where you’ve used your Microsoft account within the last 30 days. This includes any time that you signed in to your account, whether you used a web browser, your phone, an email app, a third-party app, or another method.
- Facebook Security and Login – The features of Facebook Login such as access tokens and permissions make it safe and secure for people and apps to use, but there are some security steps that apps need to implement themselves.
- Yahoo Recent Activity – See something suspicious? Change your password
You should recognize most of the account activity in this section. If you know that you didn’t initiate one of them, or if you see a suspicious pattern (like multiple sign-in attempts or profile changes you didn’t make), don’t panic! Did you login at a cybercafe? Is your office using a VPN? A VPN will re-router your location, therefore it appears as if you are surfing the net from another country.
B) Remove Anti-Theft / Trojan Malware / Keylogger
A bad breakup is unfortunate, made worse if your ex-bf or ex-gf is into computers and has easy access to your laptop. With a few simple legal software such as anti-theft or parental control tools, he or she can easily access your laptop’s microphone, webcam and more. With a Trojan Horse and Keylogger installed, password will be delivered to his or her email, providing him with access to your personal data. Here are the various ways of protecting yourself from that crazy sociopath physco from stalking you.
Just like a knife, it can be used for cooking or killing. An anti-theft software or parental control tool for laptops or mobile phones can be used with bad intentions, it can’t capture password or user login but screenshots of your activities can be emailed to the perpetrator, almost as good as losing your password. A trojan on the other hand sends all of your personal information such as username, login password, credit card details and activities to the recipient. Both are equally bad, and should be dealt with immediately.
- 23 Free Standalone Portable Offline Antivirus Scanners
- 7 Laptop Theft Recovering Software with GPS Location Tracking and SpyCam
The easiest way to hack someone’s email illegally is via keylogger, all they need is to have access to the person’s computer, disable the antivirus and install a password capturing software. However, this will be a problem if he or she enables mobile notification for new devices logging into the account.
C) Enhance Security With 2-Step SMS Verification
Your password protects your account. You can also add a second layer of protection with 2-Step Verification, which sends a single-use code to your phone for you to enter when you sign in. So even if somebody manages to steal your password, it is not enough to get into your account. The other reason to activate 2 step verification is because they have the habit of using the same password for all accounts, hackers that managed to hack other less secure companies will ‘guess’ their way into your account.
- Microsoft Two-Step Verification
- Google 2 Step verification
- Facebook Two-Factor Authentication
- Yahoo Two-Step SMS Verification
More often than not, 2 step verification comes with mobile notifications, enable it and you will receive login alerts as an extra security feature. When you turn on login alerts, they’ll send you a text message, email or notification each time someone (including yourself) logs into your account from a new place or new device.
D) Update Secret Questions
The other method for someone to gain access to your account is to guess your secret questions and birth date correctly, by doing so, they will be able to reset your password. Without 2-Step SMS Verification enabled, you will lose access to your accounts. Remember how most of Apple’s iPhone users from Hollywood got exposed for their lewd photos?
Simply because their secret questions are too simple, such as where is your birth place, what’s your mother’s maiden name, what is the name of your pet. Being celebrities, most of the information is 1 google away, that’s how they got access into your photo gallery and downloaded everything to your comps.
Do not use the default questions, customize the question and only you know the answer to it. If possible, the question must not make any sense but only to you yourself.
- [ Bad Question ] What is your pet’s name?
- [ Bad Question ] In what year was your father born?
- [ Bad Question ] What is your favorite _____?
- [ Bad Question ] What was the name of your elementary / primary school?
E) Install Antivirus With Firewall
How do you protect yourself and prevent hackers from stealing your password? Even if nobody had access to all of your accounts, there is no harm in installing a genuine copy of antivirus with a firewall. Always subscribe to the original software, avoid those from torrent. The simple reason is hackers know the reason you are downloading an antivirus is because you are not protected, therefore these ‘free’ antivirus from torrent are infected with malware.
Free antivirus comes with many limitations, depending on the vendor, most of them offer basic protection with no firewall. Updates are slow and it tends to have advertisements. If your purchasing a genuine antivirus is out of question, do try these 12 Free Antivirus For Windows 10 – Microsoft Defender Alternatives.
Top 10 Most Used Password
When it comes to password security, this is a very sad list. According to the UK’s National Cyber Security Centre, the top 10 most used passwords are:
- 123456
- 123456789
- qwerty
- password
- 1111111
- 12345678
- abc123
- 1234567
- password1
- 12345





Most legit hackers dont use platform that compromise them, which is why they use protonmail mostly. That was what “fisthack” told me when I contacted him for a job last month