Which is the best endpoint security solution for small business, enterprise and large corporations? With the recent ransomware attack involving USD5 million bitcoin that shuts down the colonial pipeline, crippling part of the USA, it goes to show that investing in a good security software saves time and money in the long run.
Continue ➤ 5 Free Corporate Antivirus Firewall Solutions For Small Business Commercial Use
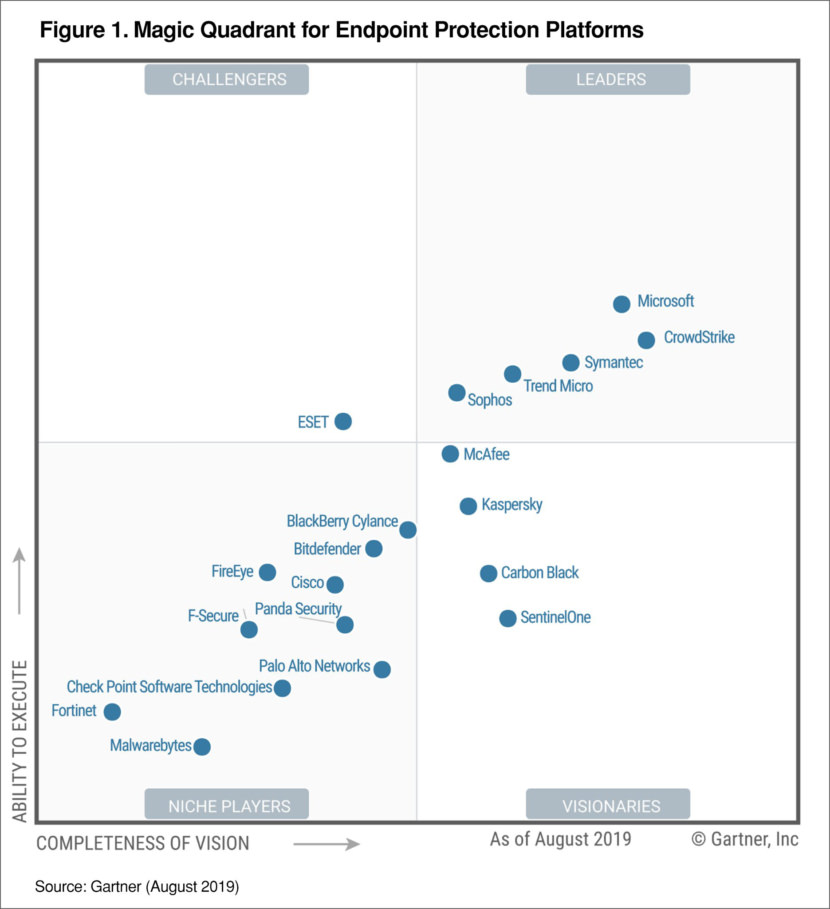
According to Gartner research, Crowdstrike, Microsoft, Symantec, Trend Micro and Sophos are 5 of the best security solution experts in the market, they are all leaders in their respective field. For your information, these are all paid software and they are not free.
Cyber attacks and data breaches are on the rise and continue to pose serious threats to their digital economy. New and existing infrastructure, including Internet backbones, mobile and fixed broadband networks, data centres, and cloud-based platforms, are constantly being exposed to these threats.
Today’s hackers have an evolving arsenal of tools that can penetrate both public and private networks and attack vulnerable systems, devices and programs. To protect business assets and customer privacy, it is imperative that an enterprise’s security be continuously maintained and improved to effectively guard against internal and external threats.
1. Microsoft Business Security Solutions
Enable Zero Trust with Microsoft security solutions, you can reduce risks by implementing a Zero Trust security model, validating identities and device compliance for every access request. Microsoft Security is a Leader in five Magic Quadrants — access management, unified endpoint management tools, cloud access security brokers, enterprise information archiving, and endpoint protection platforms.
- Protect and govern sensitive data – Safeguard data across clouds, apps, and endpoints by configuring protection and retention labels.
- Identify and remediate risks – Prevent, investigate, and remediate both malicious and inadvertent activities within your organization.
- Simplify compliance management – Assess, improve, and monitor compliance to address legal and regulatory compliance requirements.
- Secure your apps and resources across clouds – Safeguard your entire cloud estate with complete visibility and comprehensive protection across workloads.
- Stop threats with integrated, automated protection – Secure your business with security information and event management (SIEM) and extended detection and response (XDR).
- Protect identities and manage access – Safeguard access to resources with a complete identity solution that securely connects all your users, apps, and devices.
2. Crowdstrike
Healthcare / Finance / Retail / Gov / Education
CrowdStrike is a leader in cloud-delivered, next-generation services for endpoint protection, threat intelligence, and response. The CrowdStrike Falcon platform stops breaches by preventing and responding to all types of attacks—both malware and malware-free. CrowdStrike is the pioneer of cloud-delivered endpoint protection. CrowdStrike Falcon has revolutionized endpoint security by being the first and only solution.
- Improve decision making – Gather insights and details about your cloud workload, and container — images, registries, libraries and containers spun from those images.
- Uncover hidden threats – Find hidden malware, embedded secrets, configuration issues and more in your images to help reduce the attack surface.
- Gain visibility into container environments – Get full visibility into running containers to uncover details surrounding file access, network communications and process activity.
- Identify vulnerabilities faster – Save valuable time with pre-built image scanning policies enabling you to quickly catch vulnerabilities, misconfigurations, and more.
- Eliminate threats prior to production – Block exploitable vulnerabilities based on IOAs before runtime, eliminating headaches for security teams.
- Continuously monitor – Identify new vulnerabilities at runtime, alert and take action without having to rescan images.
3. Broadcom’s Symantec
Industry analysts across the globe have named Broadcom’s Symantec as a global leader in Endpoint Security, Web Security, Information Security, Email Security, and Privileged Access Management. They have over 2,800 patents and are the only company with the scale, right complement of products, and foundational portfolio to deliver comprehensive, integrated, and industry-leading cyber defense for enterprises and large corporation all over the globe.
- Endpoint Security – Endpoints are the critical last line of defense against cyber attackers. Symantec Endpoint Security solutions prevent, harden, detect, and respond to emerging threats across laptops, desktops, tablets, mobile phones, servers, and cloud workloads.
- Identity Security – User identities are under attack by cyber criminals hoping to exploit their access and privileges and do harm. Symantec mitigates these attacks by enforcing granular security policies to stop unauthorized access to sensitive resources and data.
- Information Security – Symantec offers integrated information security solutions to help you protect sensitive data everywhere it goes – across endpoints, cloud services, private apps, and on-premises.
- Network Security – Email and web access are the lifeblood and essential communication means for every modern organization. Symantec has a full array of network security solutions, as well as a shared set of advanced threat protection technologies.
4. Trend Micro
Healthcare / Manufacturing
Trend Micro is the global leader in enterprise data security and cybersecurity solutions for businesses, data centres, cloud environments, and networks. It is perhaps the only Japanese company among the security software industry, also known as Torendo Maikuro Kabushiki-Gaisha), Trend Micro is an American-Japanese multinational cyber security software company with global headquarters in Tokyo, Japan and Irving, Texas, United States, with regional headquarters and R&D centers in Asia, Europe, and North America.
- Enterprise Ransomware Protection – There is no silver bullet when it comes to ransomware, so you need a multi-layered approach, prioritized for the best risk mitigation. The four layers are all infused with XGen™ security, a cross-generational blend of threat defence techniques that intelligently applies the right technology at the right time.
- Protecting End-of-Support Systems – The end of support for leading enterprise platforms, such as the outdated Windows 95, Windows XP, Windows NT, Windows Vista, Windows Server 2008 and Server 2008 R2, can introduce major challenges for organisations running mission-critical applications. Continuing to use platforms and applications that have reached end of support leaves organisations exposed to new vulnerabilities, malware threats, and data breaches. Trend Micro™ Deep Security™ delivers leading automated protection to secure your applications and workloads across new and EOS systems. Deep Security’s virtual patching automatically shields systems from new threats and vulnerabilities, minimising disruptions and ensuring your critical applications and sensitive enterprise data stay protected.
5. Sophos
Healthcare / Finance Banking / Gov / Education
Sophos XDR goes beyond the endpoint and server, pulling in firewall, email and other data sources*. You get a holistic view of your organization’s cybersecurity posture with the ability to drill down into granular detail when needed. Adding more Sophos XDR enabled products gives you access to even more visibility and context. With data from each product flowing into the Sophos Data Lake you can quickly find critical information and ensure you have the most complete view of your network.
- Public Cloud – Secure cloud infrastructure, ensure compliance, and find ways to optimize cloud spend. Protecting Kubernetes clusters, Amazon Web Services, Microsoft Azure, Google Cloud Platform, and Infrastructure-as-Code environments from the latest threats and configuration vulnerabilities from the Sophos Central single-management console.
- Sophos Firewall – Sophos Firewall delivers enterprise-grade protection, unmatched risk visibility, and all the flexibility you need to power today’s most demanding distributed networks.
- Endpoint Protection – Stops malware, ransomware, exploits, and viruses. Achieve unmatched endpoint threat prevention. Intercept X uses deep learning, an advanced form of machine learning to detect both known and unknown malware without relying on signatures.