How to be completely anonymous on the internet? There are many tools to mask and protect your identity online. These tools are useful when you are browsing the internet in China, Iran, Saudi Arabia, Russia or any country that ranks lowly in freedom of speech and journalism.
Continue ➤ 14 Free VPN With Servers In USA And UK For Torrenting – 100% Secure & Anonymous
The best way to protect your privacy is to always use a VPN, reason being that everytime you log onto the internet, you are broadcasting your computer ID and more, therefore with a little bit of investigating, you can be tracked. If you cannot move away from using Windows or macOS, try and get another laptop and install TailOS.
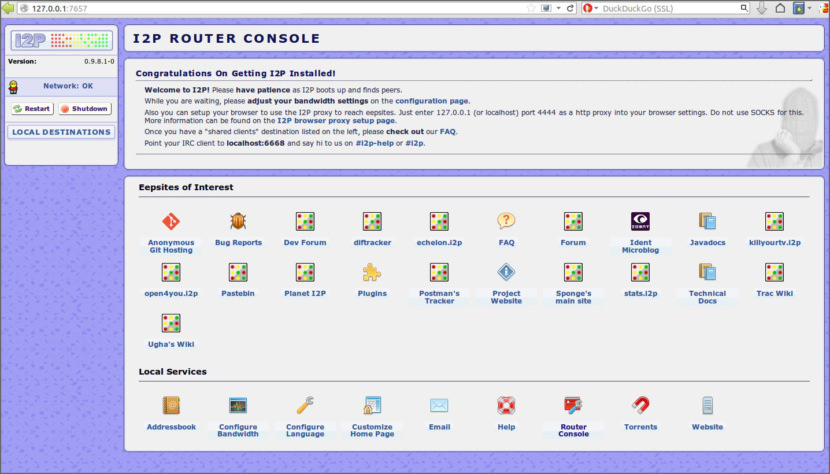
1. I2P
Network | Windows | macOS | Linux | Android
The I2P network provides strong privacy protections for communication over the Internet. Many activities that would risk your privacy on the public Internet can be conducted anonymously inside I2P. I2P is an anonymous overlay network – a network within a network. It is intended to protect communication from dragnet surveillance and monitoring by third parties such as ISPs. What can you do with I2P?
- Email: Integrated web mail interface, plugin for serverless email.
- Web browsing: Anonymous websites, gateways to and from the public Internet.
- Blogging and forums: Blogging and Syndie plugins.
- Website hosting: Integrated anonymous web server.
- Real-time chat: Instant messaging and IRC clients.
- File sharing: ED2K and Gnutella clients, integrated BitTorrent client.
- Decentralized file storage: Tahoe-LAFS distributed file system plugin.
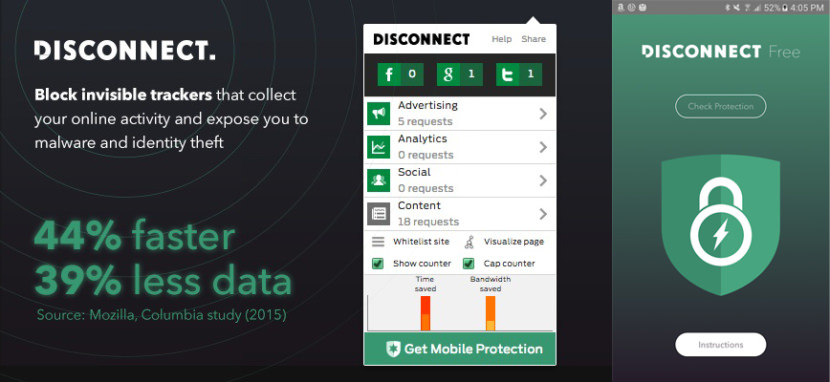
2. Disconnect Basic
VPN | Chrome | Safari | Firefox | Opera | Android
Their privacy policy, in a sentence: They don’t collect your IP address or any other personal info, except the info you volunteer. Make the web faster, more private, and more secure. Disconnect lets you visualize and block the invisible websites that track you. Load the pages you go to 44% faster. Stop tracking by thousands of third-party sites.
Disconnect was named the best privacy tool by the New York Times (2016), Innovation Award winner for Best Privacy and Security software at South by Southwest (2015), listed as one of the 100 best innovations of the year by Popular Science and one of the 20 best Chrome extensions by Lifehacker.
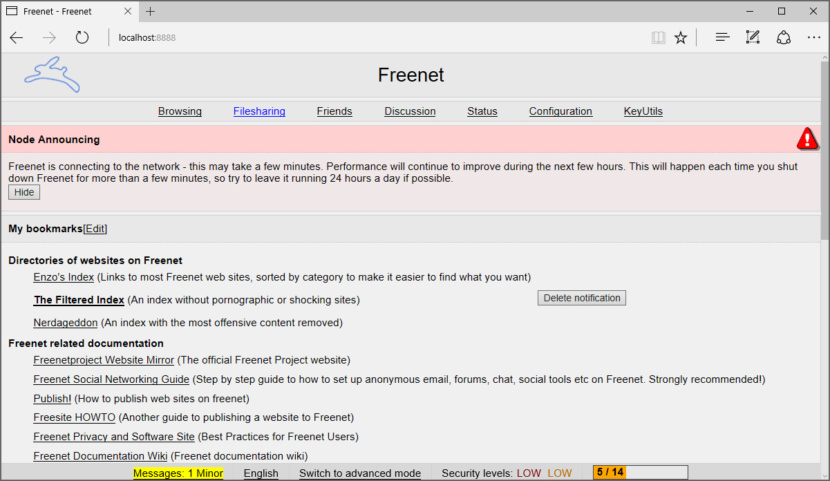
3. Hyphanet a.k.a Freenet
Network | Windows | macOS | Linux
Freenet is free software which lets you anonymously share files, browse and publish “free sites” (web sites accessible only through Freenet) and chat on forums, without fear of censorship. Freenet is decentralised to make it less vulnerable to attack, and if used in “darknet” mode, where users only connect to their friends, is very difficult to detect.
Users contribute to the network by giving bandwidth and a portion of their hard drive (called the “data store”) for storing files. Files are automatically kept or deleted depending on how popular they are, with the least popular being discarded to make way for newer or more popular content. Files are encrypted, so generally the user cannot easily discover what is in his datastore, and hopefully can’t be held accountable for it. Chat forums, websites, and search functionality, are all built on top of this distributed data store.
4. Whonix
Bootable OS | Windows | macOS | Linux
Whonix is a desktop operating system designed for advanced security and privacy. Whonix mitigates the threat of common attack vectors while maintaining usability. Online anonymity is realized via fail-safe, automatic, and desktop-wide use of the Tor network. A heavily reconfigured Debian base is run inside multiple virtual machines, providing a substantial layer of protection from malware and IP address leaks. Commonly used applications are pre-installed and safely pre-configured for immediate use.
- Based on Tor – Whonix utilizes Tor’s free software, which provides an open and distributed relay network to defend against network surveillance.
- Isolation – Connections through Tor are enforced. DNS leaks are impossible, and even malware with root privileges cannot discover the user’s real IP address.
- Compatibility – Whonix is available for all major operating systems. Most commonly used applications are compatible with the Whonix design.
5. Tor Browser
Browser & Network | Windows | macOS | Linux
The Tor software protects you by bouncing your communications around a distributed network of relays run by volunteers all around the world: it prevents somebody watching your Internet connection from learning what sites you visit, it prevents the sites you visit from learning your physical location, and it lets you access sites which are blocked.
Tor Browser lets you use Tor on Microsoft Windows, Apple MacOS, or GNU/Linux without needing to install any software. It can run off a USB flash drive, comes with a pre-configured web browser to protect your anonymity, and is self-contained (portable).
6. Tails
Bootable OS | Windows | macOS | Linux
Tails is a live operating system that you can start on almost any computer from a USB stick or a DVD. Tails is a live system that aims to preserve your privacy and anonymity. It helps you to use the Internet anonymously and circumvent censorship almost anywhere you go and on any computer but leaving no trace unless you ask it explicitly. It aims at preserving your privacy and anonymity, and helps you to:
- use the Internet anonymously and circumvent censorship;
- all connections to the Internet are forced to go through the Tor network;
- leave no trace on the computer you are using unless you ask it explicitly;
- use state-of-the-art cryptographic tools to encrypt your files, emails and instant messaging.




I think now almost everyone knows and uses VPN and tor, but you also need to replace all social networks with anonymous messengers, such as jabber or Utopia